

Vision
Networks make it easy to establish ad hoc collaborating communities of
people and computing devices. They configure and reconfigure themselves
automatically, as nodes appear, migrate, and disappear. This makes them easier
to maintain than before, when networks were tuned largely for static wired
topologies. Local networks connect seamlessly with each other, with satellite
and terrestrial networks, and with a large number and variety of physical
devices that can be used to monitor and control the physical world.
 Networks make it easy to locate resources, both nearby and further away, using
names that express what is needed (e.g., "the nearest available
printer"), rather than where to find it (e.g., myprinter.mynet.com).
This makes them more useful and more resilient to failures, load conditions,
and resource mobility.
Networks make it easy to locate resources, both nearby and further away, using
names that express what is needed (e.g., "the nearest available
printer"), rather than where to find it (e.g., myprinter.mynet.com).
This makes them more useful and more resilient to failures, load conditions,
and resource mobility.
Networks route heterogeneous traffic efficiently, in response to application
demands, through nodes that differ in connectivity, computational power, and
resources. They adapt to current channel conditions, no longer treating all
channels as "leaky pipes" with fixed and known diameters (peak bandwidths) and
loss characteristics. This adaptability is essential for wireless channels,
whose peak bandwidth and error characteristics can vary dynamically and
unpredictably. RF channels, for example, are affected by terrain, weather, and
interference from other transmitters. Networks respond flexibly to such
unpredictability. Instead of sending all packets at low data rates or
broadcasting at high power, they allow applications to trade data rates off
against energy consumption. Instead of always using complex and costly error
correction, they use only as much as applications require. Instead of being
designed to handle unlikely combinations of worst-case conditions, they are
designed more economically to handle current or common conditions.
Approach
Flexible, decentralized networks, called N21s, connect dynamically
changing configurations of self-identifying mobile and stationary devices.
N21s integrate different wireless, terrestrial, and satellite networks into one
seamless internet. Through algorithms, protocols, and middleware, they
- configure collaborative regions automatically, creating topologies and adapting them to mobility and change,
- provide automatic resource and location discovery, without manual configuration and administration,
- provide secure, authenticated, and private access to networked resources, and
- adapt to changing network conditions, including congestion, wireless errors, latency variations, and heterogeneous traffic (e.g., audio, video, and data), by balancing bandwidth, latency, energy consumption, and application requirements.
Collaborative regions
Collaborative regions are self-organizing collections of computers and/or
devices that share some degree of trust. Computers and devices may belong
to several regions at the same time. Membership is dynamic: mobile
devices may enter and leave different regions as they move around.
Collaborative regions employ different protocols for intra-space and
inter-space communication because of the need to maintain trust.
Resource and location discovery
N21 networks enable applications to use intentional names, not just
location-based names, to describe the information and functionality they are
looking for. Intentional names support resource discovery by providing access
to entities that cannot be named statically, such as a full soda machine or to
the surveillance cameras that have recently detected suspicious activity.
N21 networks integrate name resolution and routing. Intra-space routing protocols perform resolution and forwarding based on queries that express the characteristics of the desired data or resources in a collaborative region. Late binding between names and addresses (i.e., at delivery time) supports mobility and multicast. Early binding supports high bandwidth streams and anycast. Wide-area routing uses a scalable resolver architecture; techniques for soft state and caching provide scalability and fault tolerance.
N21 networks support location discovery through proximity to named physical objects (for example, low-power RF beacons embedded in the walls of buildings). Location discovery enables mobile devices to access and present location-specific information. For example, an H21 might help visitors navigate to their destination with spoken right-left instructions; held up next to a paper or an electronic poster of an old talk, it could provide access to stored audio and video fragments of the talk; pointed to a door, it could provide information about what is happening behind the door.
Security
A collaborative region is a set of devices that have been instructed by their
owners to trust each other to a specified degree. A collaborative region that
defines a meeting, for example, has a set of trust and authorization rules that
specify what happens during a meeting (how working materials and presentation
illustrations are shared, who can print on the local printer). Typically,
trust rules for a meeting do not allow participants to write arbitrary
information anywhere in the region. However, once users know what the trust
rules are, they can introduce their devices into the meeting's collaborative
region, with confidence that only the expected range of actions will happen,
even if the details of the interactions are left to automatic configuration.
Resource and location discovery systems address privacy issues by giving resources and users control over how much to reveal. Rather than tracking the identity, location, and characteristics of all resources and users at all times, these systems accept and propagate only the information that resources and users choose to advertise. Self-certifying names enable clients of discovery systems to trust the advertised information.
Adaptation
N21 networks allow devices to use multiple communication protocols. Vertical
handoffs among these protocols allow H21 devices to provide seamless and power
efficient connectivity across a wide range of domains, for example,
building-wide, campus wide, and point-to-point. They also enable applications
to adapt to changes in channel conditions (e.g., congestion and packet loss)
and in their own requirements (e.g., for bandwidth, latency, or reliability).
They provide interfaces to monitoring mechanisms, which allow end-host
transport agents to learn about congestion or about packet losses caused by
wireless channel errors. This enables end-to-end resource management based on
a unified congestion manager, which provides different flows with "shared state
learning" and allows applications to adapt to congestion in ways that
accommodate the heterogeneous nature of streams. Unlike the standard TCP
protocol, which is tuned for bulk data transfers, the congestion manager
efficiently handles congestion due to audio, video, and other real-time
streaming applications, as well as to multiple short connections. N21 networks
provide interfaces to control mechanisms, which enable applications to
influence the way their packets are routed.
Oxygen Today
Dynamic networks
 Grid is a routing protocol for
ad-hoc mobile wireless networks. It is self-configuring and does not require
any fixed infrastructure such as base stations or access points. Instead, Grid
nodes cooperatively forward each other's data. A Grid network can be deployed
rapidly, is robust in the face of node failures, and intrinsically supports
mobile hosts. (Robert Morris,
Parallel and Distributed Operating
Systems)
Grid is a routing protocol for
ad-hoc mobile wireless networks. It is self-configuring and does not require
any fixed infrastructure such as base stations or access points. Instead, Grid
nodes cooperatively forward each other's data. A Grid network can be deployed
rapidly, is robust in the face of node failures, and intrinsically supports
mobile hosts. (Robert Morris,
Parallel and Distributed Operating
Systems)
Span is a topology maintenance protocol for energy efficient, ad-hoc wireless
networks. Since idle receive circuits consume almost as much power listening
for packets as do active circuits when receiving packets, Span nodes save power
by turning off their radio receivers most of the time. Nonetheless, they
forward packets between any source and destination with a delay close to a
standard 802.11 ad-hoc network, and the topology formed by awake nodes provides
about as much total capacity as the original network. (Hari Balakrishnan, Networks and Mobile Systems; Robert Morris, Parallel and Distributed Operating Systems)
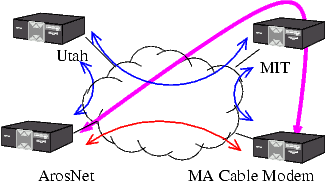 A Resiliant Overlay Network (RON)
allows distributed Internet applications to detect and recover from path
outages and periods of degraded performance within several seconds, improving
over today's wide-area routing protocols that take at least several minutes to
recover. RON nodes use active measurements to monitor the functioning and
quality of the Internet paths among themselves, and use this information to
decide whether to route packets directly over the Internet or by way of other
RON nodes, optimizing the path using application-specific routing metrics. (Hari Balakrishnan, Networks and Mobile Systems; M. Frans Kaashoek, Robert Morris, Parallel and Distributed Operating Systems)
A Resiliant Overlay Network (RON)
allows distributed Internet applications to detect and recover from path
outages and periods of degraded performance within several seconds, improving
over today's wide-area routing protocols that take at least several minutes to
recover. RON nodes use active measurements to monitor the functioning and
quality of the Internet paths among themselves, and use this information to
decide whether to route packets directly over the Internet or by way of other
RON nodes, optimizing the path using application-specific routing metrics. (Hari Balakrishnan, Networks and Mobile Systems; M. Frans Kaashoek, Robert Morris, Parallel and Distributed Operating Systems)
Chord is a scalable distributed
lookup protocol for peer-to-peer networks. Chord maps keys to nodes, adapting
efficiently as nodes join and leave the system. Communication costs and the
state maintained by each node scale logarithmically with the number of Chord
nodes. The Cooperative File System
(CFS) is based on Chord
and provides highly available, read-only storage to a group of cooperating
users. (Hari Balakrishnan, Networks and Mobile Systems; M. Frans Kaashoek, Robert Morris, Parallel and Distributed Operating Systems;
David Karger, Theory of Computation)
Resource discovery
The Intentional Naming System
(INS) supports scalable, dynamic resource discovery and message delivery.
Names in INS describe application intent in the form of properties and
attributes of resources and data, not just network locations. Intentional Name
Resolvers in an application-level overlay network collaborate to store resource
information and resolve queries. Resolvers used Chord to specialize
dynamically around specific resource descriptions, distribute information
evenly among themselves, and resolve queries by visiting only a small number of
other routers. (Hari
Balakrishnan, Networks and Mobile
Systems)
Access to resources is either public or protected by SPKI/SDSI (Simple Public
Key Intrastructure / Simple Distributed Security Infrastructure) access control
lists (ACLs). Software proxies (K21s) for resources and users run either on
embedded processors or, for users and lightweight resources, on remote hosts
that communicate securely with resources using shared symmetric keys. When
using INS for resource discovery, a user's K21 proxy presents authorization
information along with an intentional query, and INS compares this information
to resource-supplied ACLs, thereby sparing the user from having to iterate
through lists of inaccessible resources while searching for an accessible one.
(Srinivas Devadas, Computation Structures Group; Ronald Rivest, Cryptography and Information
Security)
Mobility
Migrate is an end-to-end
approach to host mobility that manages session-specific application state
across changes in network attachment points and during periods of
disconnectivity. (Hari
Balakrishnan, Networks and Mobile
Systems; M. Frans
Kaashoek, Parallel and Distributed
Operating Systems)
The Self-Certifying File System
(SFS) is a secure decentralized global file system that provides users with
authenticated access to their data from any location. SFS path names
effectively contain public keys, which makes them self-certifying and
guarantees that the files being accessed indeed belong to the user. (M. Frans Kaashoek, Parallel and Distributed Operating Systems)
Network applications
The Patient-Centric Network (PCN) is a prototype multi-tiered, plug-and-play
network for hospital operating rooms. It provides a clean separation between
probes that gather data and software that processes the data. A collection of
gateways and software proxies bring sensors onto the network, perform data
fusion, and create new virtual devices. (John Guttag, Dorothy Curtis, Networks and Mobile Systems)
